Cyber attacks have become widespread and have also increased in sophistication over time. A simple oversight in your network security could trigger a series of events that could be disastrous for your business. You can avoid this by adopting a robust cyber security framework such as Zero Trust Network Access (ZTNA).
Zero trust asserts that no user or application should be automatically trusted. It encourages organisations to verify every access while considering every user or application as a potential threat. ZTNA is an excellent starting point for businesses that aim to establish a strong cyber security posture. It can not only adapt to the complexity of the modern work environment, including a hybrid workplace but also safeguard individuals, devices, applications, and data regardless of their location.
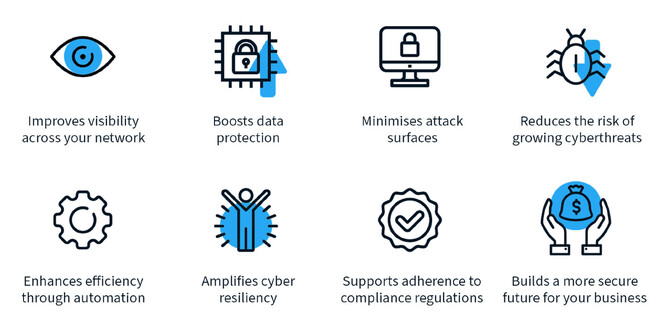
8 Key Benefits of Zero Trust
The 7 Pillars of Zero Trust
User Security
Prioritise user identity verification and authorization before granting access to requested resources to ensure a strong level of identity security.
Device Security
Enhance the security of your business environment by identifying and authenticating devices attempting to connect to your network resources.
Network/Environment Security
Establish network segments and implement real-time threat protection, encryption monitoring, and analytics to deter unauthorised access.
Applications & Workload Security
Strengthen the security of your SaaS applications and APIs by implementing proper in-app permissions and secure configurations to prevent unauthorized access and data breaches.
Data Security
Implementing a comprehensive data management strategy, including encryption during transit and storage, is crucial to preventing data exfiltration.
Visibility & Data Analytics
Leverage next-generation automated solutions to obtain real-time insights, identify abnormal patterns, and make dynamic adjustments to access policies.
Automation & Orchestration
Employ automated security tools to eliminate manual security procedures and facilitate policy-based actions across the network efficiently and swiftly.
Implementing Zero Trust
3 Core Principles to Remember
1. Continually Verify
You should strive to implement a “never trust, always verify” approach to security by continuously confirming the identity and access privileges of users, devices and applications. Consider implementing strong identity and access (IAM) controls. It will help you define roles and access privileges — ensuring only the right users can access the right information.
2. Limit Access
Misuse of privileged access is one of the most common reasons for cyberattacks. Limiting access ensures that users are granted minimal access without affecting their day-to-day activities. Here are some common security practices that organisations have adopted to limit access:
Just-in-time access (JIT) – Users, devices or applications are granted access only for a predetermined period. This helps limit the time one has access to critical systems.
Principle of least privilege (PoLP) – Users, devices or applications are granted the least access or permissions needed to perform their job role.
Segmented application access (SAA) – Users can only access permitted applications, preventing any malicious users from gaining access to the network.
3. Assume Breach & Minimize Impact
Instead of waiting for a breach, you can take a proactive step toward your cybersecurity by assuming risk. That means treating applications, services, identities and networks — both internal and external — as already compromised. This will improve your response time to a breach, minimise the damage, improve your overall security and, most importantly, protect your business.
We Can Help!
Achieving zero trust compliance on your own can be a daunting task. Managed IT can implement a Zero Trust Network Access (ZTNA) framework that enforces the principle of least privilege, giving users only the access they need to complete their tasks... and no more. Our adaptive ZTNA model, grants or denies access based on real-time assessment of user and device trustworthiness.
Your data is your business, and it should always be protected. Don't give cyber criminals an easy way in, and adopt a Zero Trust Network Access framework with our team today.